Sentinel Playbook: Device Isolation Using MDE API (Part 2 - Logic App)
In Part 1 we learned how to authenticate with the Microsoft Defender API and retrieve a list of devices. In this part 2, we’ll continue building on that by creating an Azure Logic App that isolates devices in bulk based on their Device Tag or Group.
Step 1: Designing the Logic Apps
Now we need to understand what are we going to do with Logic App. Here is the flow that we are trying to achieve by using Logic App + API. In part 1 demonstration, we have shown how we can GET Access Token and GET Defender device list.
graph LR; Trigger --> step2["API call to GET Token"] --> step3["Use token to GET device by Tag/Group"] --> step4["Loop, Use token POST to Isolate device one by one"]
Once you are ready, our next step now is to go to Logic Apps page and create new Logic App. For this demo, I will be using Consumption hosting option as I will not be using this API that much for demo purpose.
Adding Permission to LogicApp
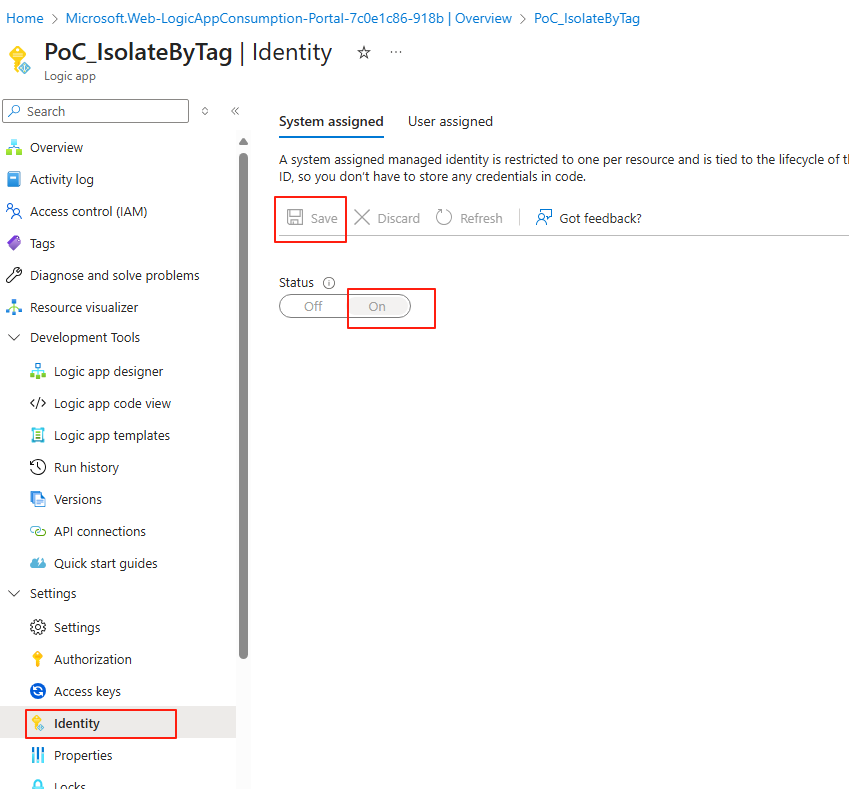
We need our Logic App to be able to read client secret that we have stored in Azure Key Vault previously. To do so, go to Logic Apps > Settings > Identity page , we need to set up Managed Identity.
Tip
Using Managed Identity means your Logic App doesn’t need to store sensitive values like client secrets directly in the workflow. This reduces the risk of exposure, and keeps your authentication process fully managed by Azure.
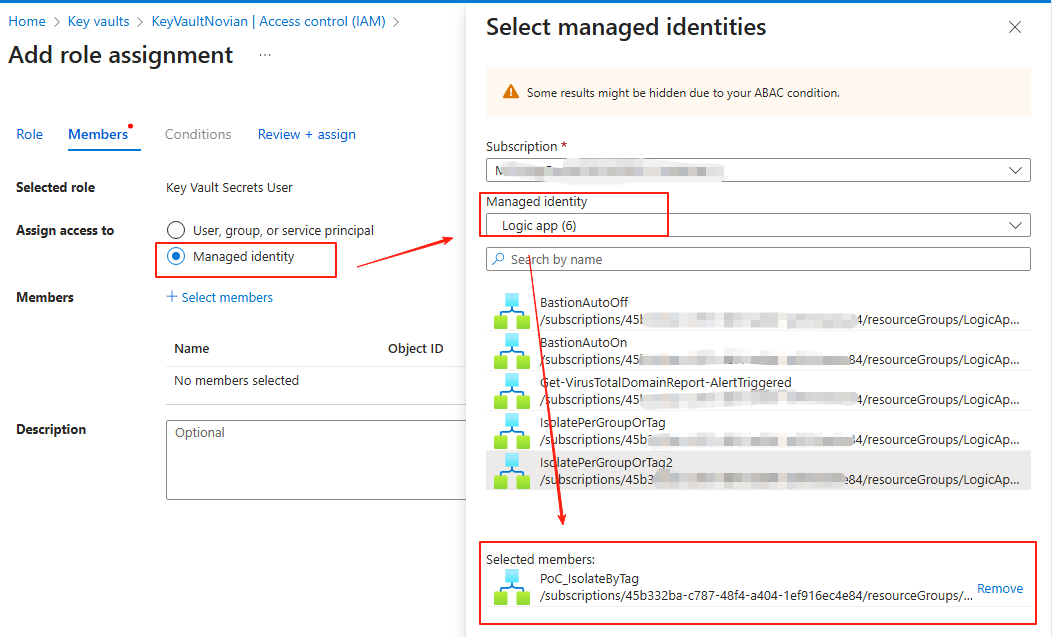
Now go to the Key Vault resource that you created in Part 1 > Access control (IAM) > Add, you want to add Key Vault Secrets User > Assign access to Managed identity. Save this Assignment.

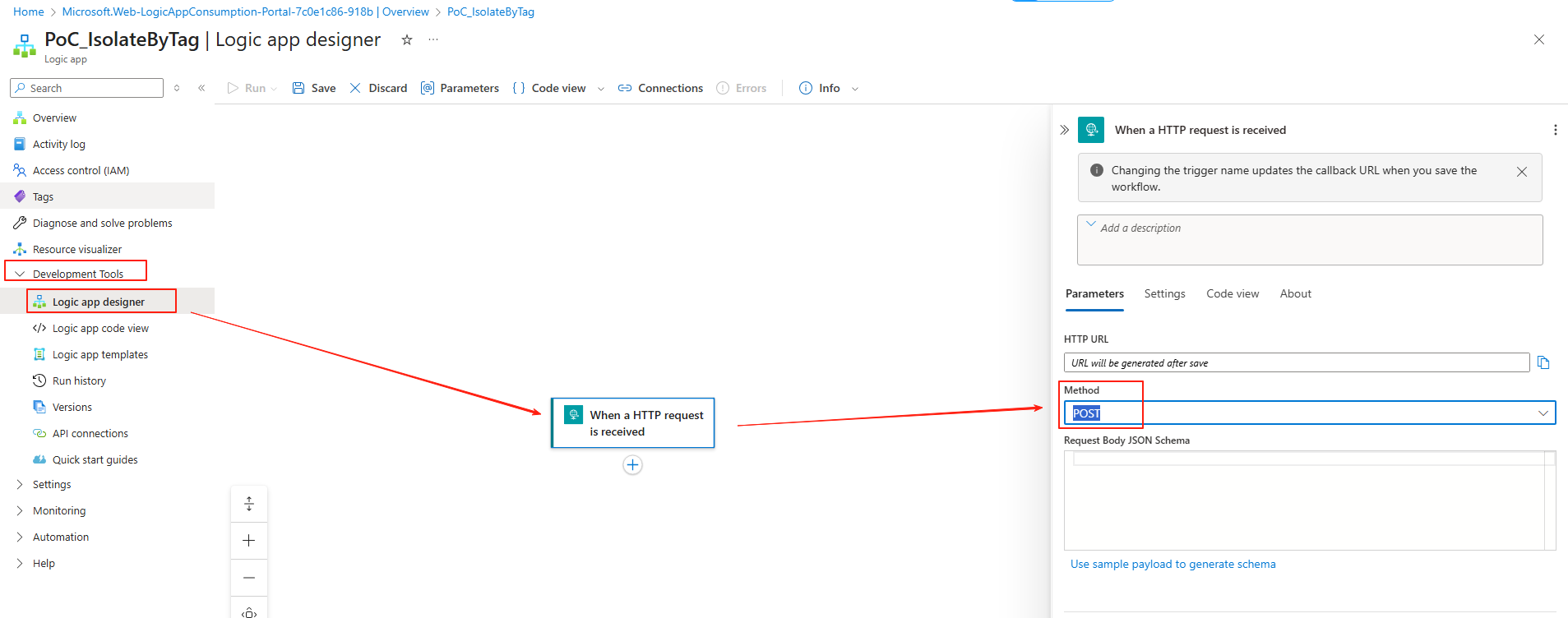
Logic App Designer - Trigger
Go to Logic app designer. As this is a proof of concept, I will use manual trigger (When a HTTP request is received), and change the method to POST. If you want to create this as automation, you can modify the trigger.

API call to GET Token
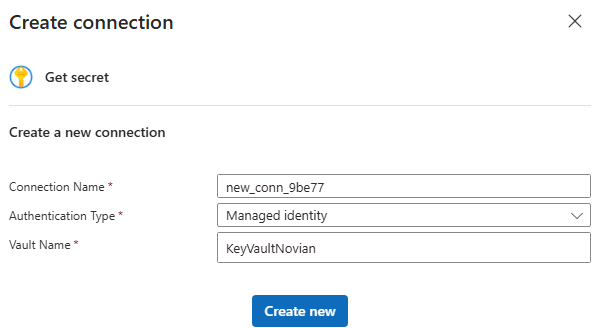
We need to retrieve the secret from Key vault. Create new action to Azure Key vault > Get secret, select Managed identity and paste your KeyVault name.

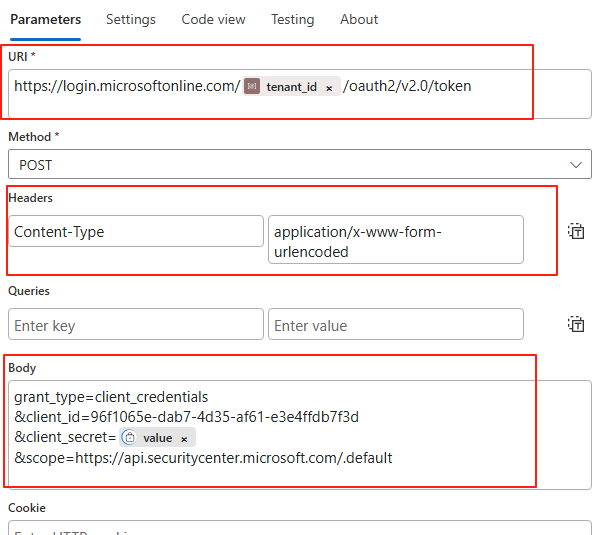
Next, we need to use these secret and to obtain our Access Token. Create new action for HTTP and enter the following information (modify the {tenant-id},{client-id} and {client-secret} accordingly):
Name: Get Token
URI:
https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/tokenHeaders:
Content-Type->application/x-www-form-urlencodedBody:
grant_type=client_credentials&client_id={client-id}&client_secret={client-secret}&scope=https://api.securitycenter.microsoft.com/.default
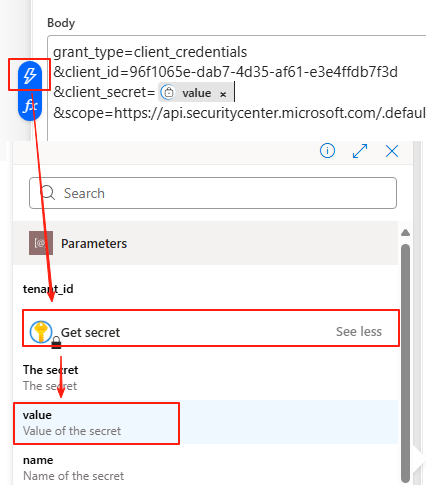
 To get the Client Secret from our Azure Key Vault, do the following:
To get the Client Secret from our Azure Key Vault, do the following:

Use token to GET device by Tag/Group
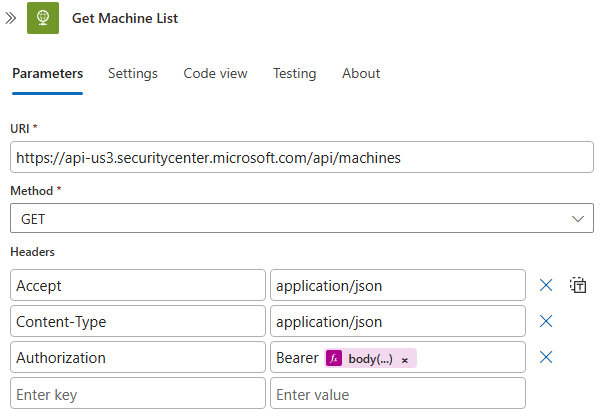
Create a next action to HTTP again, and this time use the following information:
Name: Get Machine List
URI:
https://api-us3.securitycenter.microsoft.com/api/machinesMethod: GET
Headers:
Accept->application/jsonAuthorization->Bearer @{body('Get_Token')?['access_token']}Content-Type->application/json
And since we want to filter it based on Device Tag in this example, create new action to Data Operations > Filter Array, input the following information:
Name: Filter for DeviceTag
From:
@{body('Get_Machine_List')?['value']}Filter Query:
@contains(@{item()?['machineTags']},"TestTag")
Info
In above example we will use manual/static Device Tag TestTag. For Incident automation scenario you might want to get this information from your trigger, using the Dynamic function.
Quick Sanity Check
Do a quick check, lets Run our Logic Apps, and see the result from top right Notification section > Open Run. You should be seeing something similar to this. Under the Outputs, now it only shows JSON details of devices with TestTag Machine Tag.
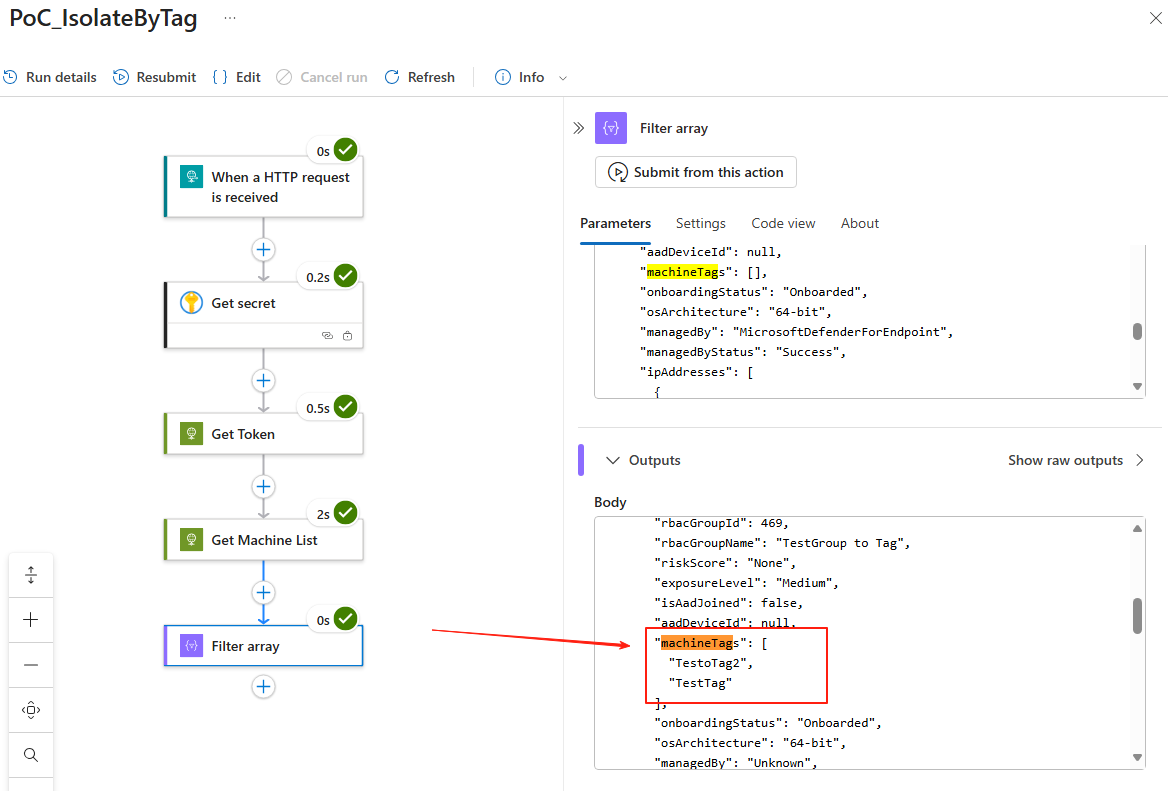

Loop, Use token to POST Isolate device one by one
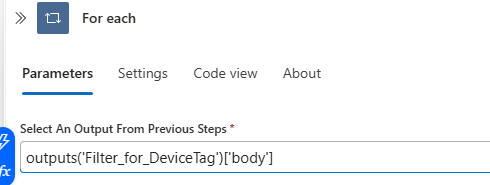
Now lets use the filtered data to Loop and execute Isolation one by one. Lets create our next action, For each and at the field Select an output from previous steps input @{outputs('Filter_for_DeviceTag')['body']}.

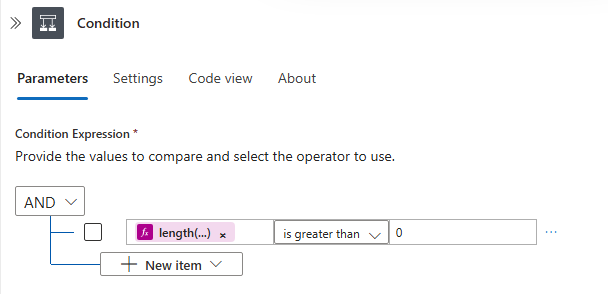
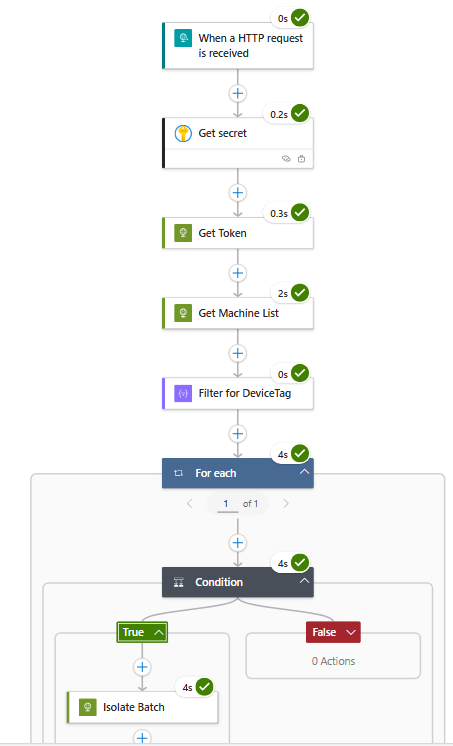
Create new action inside the loop, and create Condition. We will use this as our safeguard, this safeguard ensures that the isolation command only runs when the filtered list is not empty. Without it, a wrong filter could isolate all devices in your tenant.
. Inside the condition:
Inside the True condition, we want to create new Action > HTTP.
Name: Isolate Batch
URI:
https://api.securitycenter.microsoft.com/api/machines/@{item()?['id']}/isolateMethod: POST
Headers:
Content Type->application/jsonAuthorization->Bearer @{body('Get_Token')?['access_token']}Body:
{"Comment": "Isolating device due to suspicious activity","IsolationType": "Full"}
Step 2: Testing and Confirming
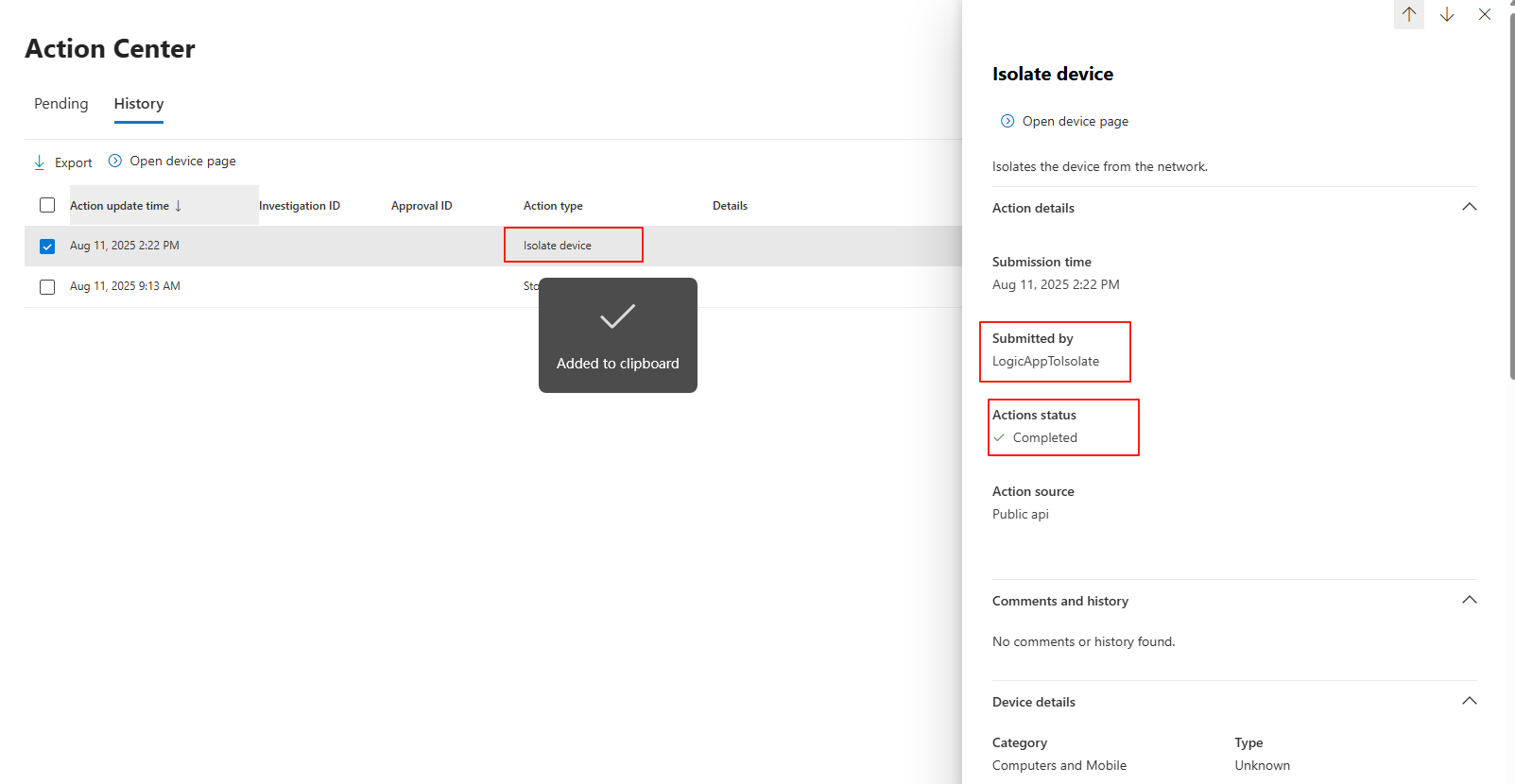
Thats all the set up you need from Logic App. Now I will test this by manually Run the Logic Apps, and it should send isolate command to devices in my environment with the “TestTag” Device Tag. You will see the result flow.

Now go to Security Portal > Investigation & response > Actions & submission > Action center > History, you should see the Isolate device command being sent by Logic App.

Wrapping Up: Whats Next?
With this setup, you now have a working Logic App that can securely fetch API credentials from Key Vault, query Defender for devices by tag, and isolate them in bulk — all with a single click (or based on trigger without manual intervention).
From here, you can take this proof of concept further by:
- Automating triggers — e.g., start the workflow automatically when a high-severity incident is detected in Microsoft Sentinel.
- More Filtering — isolate based on alert category, severity, or custom metadata instead of a static Device Tag.
This workflow not only streamlines incident response but also shows how combining Defender APIs with Logic Apps can build powerful, automated security operations.